Why Online Privacy Does Not Work…For Everyone
Warning: Undefined variable $PostID in /home2/comelews/wr1te.com/wp-content/themes/adWhiteBullet/single.php on line 66
Warning: Undefined variable $PostID in /home2/comelews/wr1te.com/wp-content/themes/adWhiteBullet/single.php on line 67
|
| Uncategorized Category RSS Feed - Subscribe to the feed here |
|
|
Highly encrypted interaction platforms, including iMessage, WhatsApp, Signal and Facebook, remain in typical usage, enabling users to send messages that can only be read by the intended recipients. There are countless legitimate factors law-abiding people may use them. And monitoring systems, no matter how well-intentioned, might be and have negative effects used for various functions or by different people than those they were developed for.
 Many different surveillance systems frequently produce unexpected results. Based on some ideas, the style stressed consistent monitoring and mental control rather than corporal penalty.
Many different surveillance systems frequently produce unexpected results. Based on some ideas, the style stressed consistent monitoring and mental control rather than corporal penalty.
 From 2006 onwards, Facebook established a privacy-invading device planned to assist in making money through targeted marketing. Facebook’s system has considering that been abused by Cambridge Analytica and others for political control, with devastating repercussions for some democracies.
From 2006 onwards, Facebook established a privacy-invading device planned to assist in making money through targeted marketing. Facebook’s system has considering that been abused by Cambridge Analytica and others for political control, with devastating repercussions for some democracies.
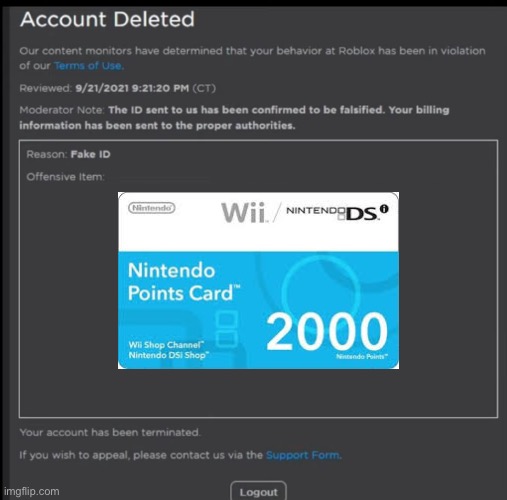
Online Privacy With Fake ID Guide
In 2018, Australia’s parliament passed the Telecommunications and Other Legislation Amendment (Assistance and Access) Act, with the apparent purpose of helping authorities to catch terrorists, paedophiles and other major wrongdoers. The act gave the Federal Police powers to “add, copy, erase or modify” material on computer systems. These powers were utilized the following year to raid a Broadcasting Corporation in connection with a story on supposed war crimes in Afghanistan.
These examples show 2 facts about security and monitoring. Security may be utilized by people of any moral character.
We for that reason need to consider what avoiding, weakening or perhaps banning the use of encrypted platforms would imply for obedient members of the community.
There are already laws that choose who is allowed to listen to communications occurring over a telecom network. While such communications are normally secured, police and national security companies can be authorised to intercept them.
Nevertheless, where communications are encrypted, companies will not immediately be able to recover the content of the conversations they obstruct. The Telecommunications and Other Legislation Amendment was passed to make it possible for companies to get support to attempt to keep their capability to get access to the unencrypted content of communications. For example, they can ask that one or more types of electronic security be gotten rid of.
There are likewise federal, state and area laws that can need people to help law enforcement and national security firms in accessing (unencrypted) information. There are likewise many proposals to clarify these laws, extend state powers and even to avoid the usage of encryption in certain scenarios. More surveillance power is not always much better and while people may hold various views on particular propositions about state powers and encryption, there are some things on which we must all be able to agree.
You might be sick of worrying about online privacy, but surveillance passiveness can also be an issue. Law enforcement and nationwide security agencies require some security powers to do their jobs. The majority of the time, this contributes to the social good of public security. Some people recognize that, sometimes it might be required to sign up on online sites with a large number of individuals and imitation specifics may wish to consider Yourfakeidforroblox.Com!
When it comes to monitoring powers, more is not always much better. We need to ask what purpose the powers serve, whether they are fairly essential for accomplishing that function, whether they are likely to accomplish the purpose, what negative consequences may result, and whether the powers are proportional. Legal use of encrypted interaction prevails and we can only develop good policy in this area if we have the facts on lawful uses of encryption.
There are numerous good factors for law-abiding citizens to use end-to-end encrypted communication platforms. Moms and dads might send out pictures or videos of their kids to trusted pals or loved ones, however prefer not to share them with 3rd parties. The explosion of tele-health throughout the COVID-19 pandemic has actually led lots of clients to clarify that they do not desire their assessment with their physician to be shared with an intermediary such as Facebook, Google, Huawei or WeChat.
As obedient citizens do have genuine reasons to rely on end-to-end file encryption, we must establish laws and policies around government monitoring appropriately. Any legislation that weakens info security across the board will have an effect on legal users as well as wrongdoers.
Find more articles written by
/home2/comelews/wr1te.com/wp-content/themes/adWhiteBullet/single.php on line 180